A Quick Guide to Chemical Safety and Security
A Quick Guide to Chemical Safety and Security
As a vital part of the Responsible Care® Initiative, CAIA and its members are committed to enhancing chemical safety and security across the entire value chain. Together, CAIA and its members seek to protect people, property, information systems, and the environment by addressing risks, vulnerabilities, and emerging threats.
As the production of chemicals expands globally, CAIA recognises the growing need for stronger security measures and compliance with legislation. Through collaborative initiatives like the Responsible Care® programme and regional partnerships, CAIA, its members, and relevant stakeholders work to ensure that the chemical industry remains secure, sustainable, and resilient in the face of emerging challenges.
Driving Continuous Improvement
Tools such as Responsible Care® and SQAS-AFRICA help evaluate and improve safety, health, environmental and security performance across the chemicals value chain.
Through these collaborative efforts, CAIA ensures that South Africa’s chemical industry remains secure, sustainable, and resilient.
Strengthening Chemical Security
Security measures are layered, graded, and based on a risk assessment of potential threats and consequences, including the misuse of:
- Acutely toxic substances
- Explosive precursors
- Chemical warfare agents and their precursors
- Solvents used in illicit drug production
- Flammables and oxidisers
- High-value or high-risk materials
Emerging Threats in Chemical Safety and Security
Modern security risks require future-ready responses. CAIA promotes the monitoring of global developments such as:
- Use of chemicals as weapons, including new synthesis technologies
- 3D printing and pharmaceutical agents that can be weaponised
- Cybersecurity vulnerabilities in automated and digital systems
- Supply chain security, ensuring chemicals do not fall into the wrong hands
- International cooperation through partners like INTERPOL and the Global Congress on Chemical Security and Emerging Threats
Regional and Global Collaboration
CAIA actively participates in regional and international initiatives to advance chemical safety and security.
Security of Chemical Facilities
Chemicals pose different risks based on their properties and the environments in which they are used. Chemical security risks should be determined through a chemical risk assessment of the likelihood and consequences of a chemical theft, release, or sabotage.
A consequence refers to the severity of loss resulting from a theft, release, or sabotage. Consequence assessments help categorise potential impacts into qualitative bands (e.g., low, medium, and high) to better understand the severity of the incident and consequence.
The severity of a loss is closely tied to the inherent hazard of the material or the potential hazard into which it may be converted.
The impact of an incident is heightened when it involves:
- High hazard chemicals
- Large quantities
- High value chemicals or equipment
- Sensitive information
The impact of an incident is heightened when it involves:
- Chemicals that are acutely toxic
- Chemical warfare agents
- Chemical warfare precursors
- Corrosive chemicals
- Explosives
- Explosives precursors
- Flammables or combustibles
- Illicit drug precursors
- Oxidisers
- Solvents used in illicit drug production
- Toxic fume releasing chemicals
- Valuable chemicals or those critical to operations
Mitigation Measures
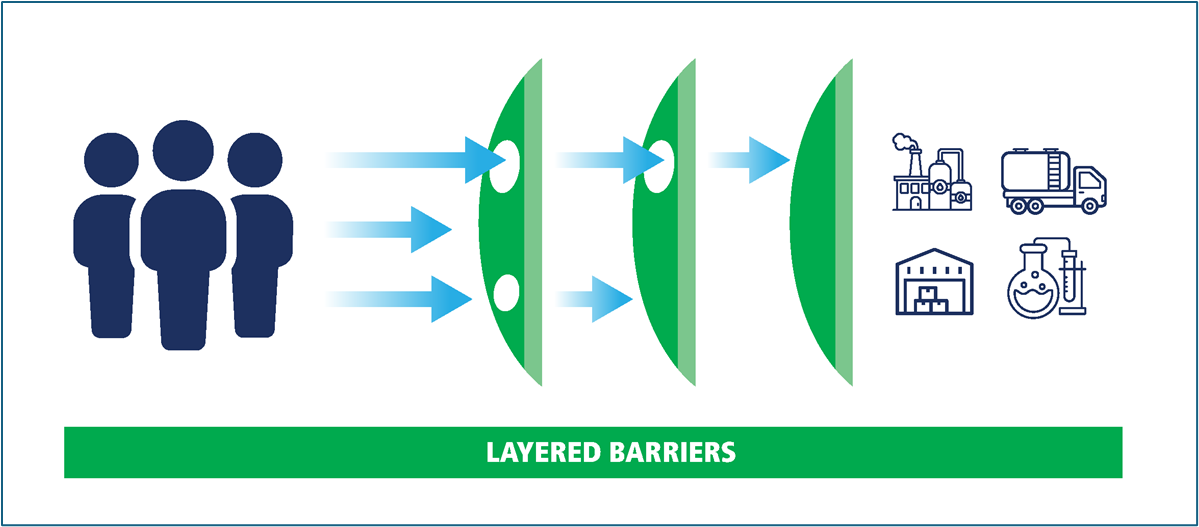
A. Physical Security
Barriers Include:
- Physical barriers i.e., walls, locks, fences, tanks, fume hoods, gates, doors, etc.
- Operational barriers i.e., procedures, inspections, checklists, etc.
- Organisational barriers i.e., signage, policies, directives, management systems, etc.
Additional types of security should also be considered such as:
1. Personnel Management
The designation of persons who are authorised to access chemicals, equipment, or other assets.
2. Inventory Management
The control and accountability of chemicals and equipment at a facility.
3. Information Security
The identification and protection of sensitive information that is valuable or could enable someone to circumvent a security system to gain unauthorised access.
4. Transport Security
The management of processes for movement of chemicals within and outside of a facility.
B. Detection
Detection increases the likelihood an intruder will be detected while attempting unauthorised access. Detection methods include sensors, access control and alarms.
C. Response
Early detection and notification are key to responding to malicious acts. This can be achieved by using security guards and/or drones for example.
D. Risk Communication
First responders, such as security guards, may need to communicate risks to law enforcement. Key information to share with law enforcement might include contact information for responsible individuals, facility layout, location, chemical inventory, process overview, and other hazards present.